The page shows an examples of the Single Sign-On to RMS using SAM2.0 with FusionAuth software self-hosted in Podman Desktop Windows.
Install FusionAuth using Podman Desktop:
•Ensure Podman Desktop (Windows) is installed.
•Open Terminal / Command prompt and execute the following:
o$podman pod create -p 5432:5432 -p 9011:9011 fusion_pod.
o$podman run --name fusion_postgres -e POSTGRES_PASSWORD=mysecretpassword -d --pod fusion_pod postgres.
o$podman run --name fusion -d --pod fusion_pod fusionauth/fusionauth-app.
•Open HeidiSQL (or any other Postgres Admin Tool):
oLogin to localhost:5432, user = postgres, password = mysecretpassword.
oCreate a new database ‘fusionauth’.
•Initial setup FusionAuth:
oOpen Browser and navigate to http://localhost:9011.
oKeep Database type settingsUnder Superuser credentials, set:
▪Username = postgres.
▪Password = mysecretpassword.
oSubmit and wait.
oEnter Admin user data (anything you like).
oAccept license and submit.
•Create RMS application:
oNavigate to http://localhost:9011/admin/.
oApplications -> +:
▪Name = rms.
▪Go to SAML tab.
▪Enable.
▪Issuer = https://rms.rotronic.com.
▪Audience: leave empty.
▪Authorized redirect URLs: add something like https://google.de, will be changed later.
▪Authentication response -> Signature canonicalization method -> change to Exclusive.
▪Save
oCustomizations -> Lambdas -> +:
▪Name = populate rms user name.
▪Type = SAML v2 populate.
▪Body:
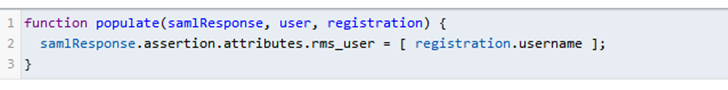
▪ Save.
oApplications -> rms -> View (green magnifying glass):
▪Scroll down to SAML v2 Integration details.
▪Copy Metadata URL value to clipboard.
Enable SAML2.0 in RMS:
•Navigate to Tools -> Setup -> System ->.
•Enable SAML2.0 SSO -> Enable SAML2.0 Login.
•Insert copied value from clipboard to IdP Metadata URL.
•Edit attribute mapping:
oUsername = rms_user.
o… add other attributes you are using.
o… if an attribute shoud be mapped from a collection, you can use array index syntax, eg. Username = usersnames[1] (for the second value from usernames property, or xxxx[-1] for the second last value of the xxx property.
•Copy SP Assertion Consumer Service URL to clipboard.
•Save.
•Navigate to Tools -> Setup -> User:
oAdd a new user with username = “testsaml2.0” and enable his “SAML2.0 Login”.
oSave.
•Logout.
Finish Configuration in FusionAuth:
•Navigate to http://localhost:9011/admin/.
•Users -> Your User -> Manage:
oRegistrations -> + Add registration.
oApplication = rms.
oUsername = testsaml2.0.
oLanguage: any.
oSave.
•Applications -> rms -> Edit -> SAML:
oAuthorized redirect URLS:
▪remove google.de.
▪add “SP Assertion Consumer Service URL” copied to clipboard from RMS setup.
oAuthentication response -> Populate lambda -> use “populate rms user name”.
oSave.
Add FusionAuth X.509 Certificate to trusted store:
•Navigate to http://localhost:9011/admin/.
•Settings -> Key Master.
•Find row with Name “SAML key generated for application rms”, download .zip and extract.
•Open Certificate manager for local machine) (certlm.msc).
•Trusted Root Certification -> Certificates -> Right Mouse Button -> All Tasks -> Import -> Select extracted ‘certificate.crt’ -> Next/Import.
Test Login:
•Navigate to RMS Login page.
•Click Log in (SAML2.0) SSO.
•Login using your FusionAuth username/password.
•You should now be logged in RMS using user “testsaml2.0”.
Updated: 20.12.2023.